Original article.
By Brian Lupo Published July 31, 2022 at 3:25 pm 166 Comments
On April 22, 2022, Kari Lake and Mark Finchem filed a complaint with the US District Court in Arizona. The complaint was a “civil rights action for declaratory and injunctive relief to prohibit the use of electronic voting machines in the State of Arizona in the upcoming 2022 Midterm Election.”
The claim insisted that the machines need to be banned from public use unless the vendors are willing to make their system open to the public.
The complaint also cited the J. Alex Halderman report that has since been sealed by Federal Judge Amy Totenberg in Curling v Raffensperger in Georgia. Initially, Halderman had requested he be allowed to at least share the report with Federal agencies so they could address the issues. Totenberg said that the Federal government could come to her if they wanted to see the report. I guess after the Williamson, TN “QR Code Mismatch” debacle where they found “erroneous code” on the machines, CISA felt they had to at least address Halderman’s findings.
CISA recently addressed the report publicly by issuing a “Security Advisory“. Part of this report listed out mitigation steps that CISA recommends be followed:

Open Records Requests in many of the controversial swing states in the 2020 election show that a majority of these mitigations were not followed in the 2020 election cycle. But rest assured: there is no evidence any of the vulnerabilities Halderman revealed in his report on the machines that were used in the 2020 election. At least that’s what they tell us hoping we will just ignore it. We won’t.
On July 21, 2022, there was a hearing for Lake v Hobbs in Phoenix. A witness by the name of Clay Parikh was called for the plaintiff. Parikh is the lead information systems security officer for the ground missile defense system for Northrop Grumman. Prior to that, he worked for Lockheed Martin and Leidos through their merger as the deputy cyber manager for the Army Corps of Engineers.
But it’s his prior work that is of particular relevance to this case: from 2008 to 2017, he worked as a security tester and a security subject matter expert for Wyle Laboratories and Pro V&V. Parikh claims to have tested hundreds of voting systems, including the Dominion and ES&S voting machines throughout his career as part of the certification process for the EAC and Secretaries of State. He holds a CISSP certification (Certified Information System Security Professional), as well as certification as an ethical hacker and a certified hacking forensics investigator.
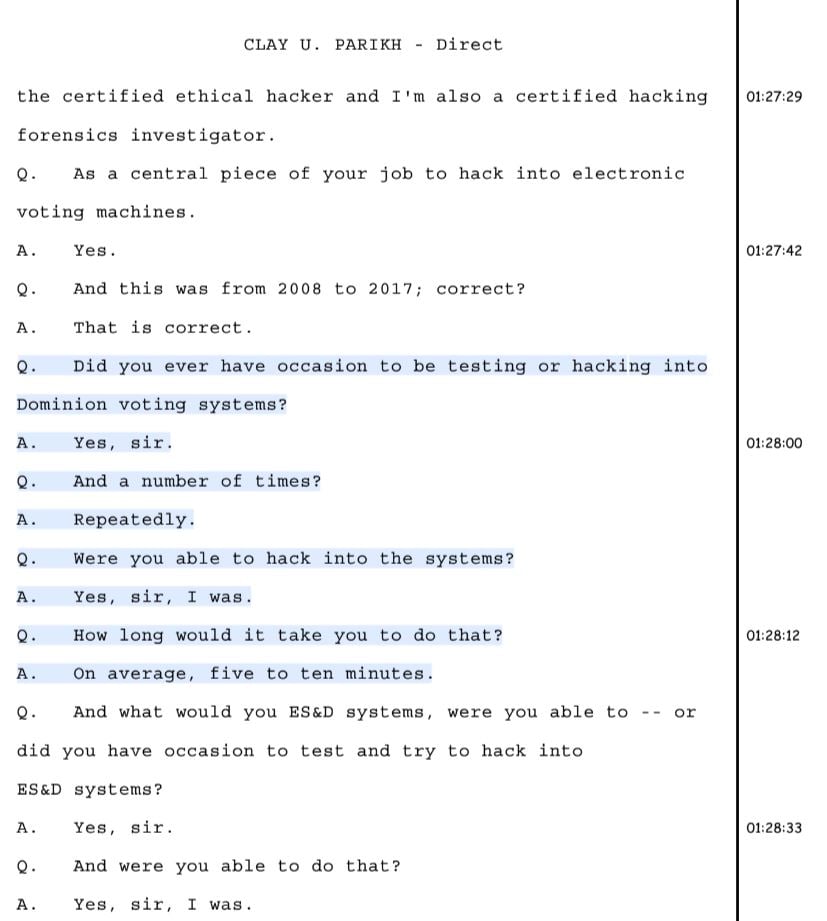
Parikh later went on to say that his “best time” hacking the ES&S machines was “two and a half minutes, but averaged five to ten minutes. It really didn’t matter to the vendor.” I wonder how that would stack up against the hackers that flock to Las Vegas for DEFCON each year for their shot at hacking these machines! As is often reported, the hackers are more often than not successful in (quickly) hacking these machines.

In cross examination, the first attorney asked if he’d worked on the exact machines used in Arizona, which Parikh responded that he had not. He then asked Parikh if he was aware Mike Lindell was financing his testimony and whether or not he knew who Mike Lindell was. The response to that was epic:

But the first attorney, in closing, took a proverbial shot over the bow when he asked Parikh to reiterate who he worked for and if his employer knew he was testifying. And the judge allowed it. How is it relevant whether or not his current employer is aware he’s testifying?

The next attorney to cross-examine Parikh was Mr. LaRue. This cross-examination was an absolute disaster.
First, we learned that the machines do in fact connect to the internet. And even when LaRue states “let’s focus on the ones that weren’t”, Parikh responded that the machines “that weren’t” still had “other available connections on the motherboards which were a concern.”

So not only did Parikh confirm that “some” machines were connected to the internet, he also confirmed that even the ones that seemingly weren’t still had available ports open to allow connection.
We’ve known for some time through the findings of Patrick Colbeck in his book “The 2020 Coup” that the ES&S DS200 machines have an Italian made Telit 4G modem chip on the motherboard. We also know that Dominion CEO John Poulos testified under oath in the Michigan State Assembly that Dominion machines did not have internet connectivity in Michigan.
LaRue also got Parikh to confess that the testing laboratories he worked for would not let him run certain tests: “…the point I’m trying to get to is…the labs told me not to do certain tests. They will not allow me to do certain tests.” Why would the testing labs try to restrict a certified tester from doing certain tests? You would think a testing lab paid by the state or local government would definitely want to ensure the machines were safe and secure no matter what testing was necessary! But that would imply that the state funds these testing labs. They don’t. The voting machine vendors pay them. You read that correctly: the voting machine companies pay the testing companies to certify that the voting machine companies software is safe and secure.
And lastly, for LaRue in his gift of a cross examination chock full of “conspiracy theory” busting truths, we find another absolute gem: Dominion updated their Democracy Suite code in 2018!
No…scratch that: it was rewritten!

And in the final redirect, plaintiff’s attorney asked about the ES&S DS200 machines. He specifically inquired if he was able to hack them and how long it took. Parikh said that he was “stopped from going further.” He said he wanted to continue and “actually get in and control the software because you can actually manipulate [sic] the statistical data on the system.”

This testimony, given under oath by Clay Parikh, changes everything.
In a 20 minute testimony with two attorneys on the cross-examination and a redirect, Clay Parikh revealed that the testing labs:
- Restrict testers from showing vulnerabilities
- Stop testers from going further into the machines in a way that could allow for software manipulation of the statistical data.
- The EAC has been sent reports of all of Parikh’s hackings, which took minutes, and were done in a professional testing environment.
- The voting machines can connect to the internet and that even the ones that aren’t connected still have open ports and means by which to connect.
- Dominion rewrote their Democracy Suite software in 2018
And most importantly:
Mike Lindell and MyPillow have the best pillows!
** End **